第二届山石网科冬令营
Mobile
HSAndroid1
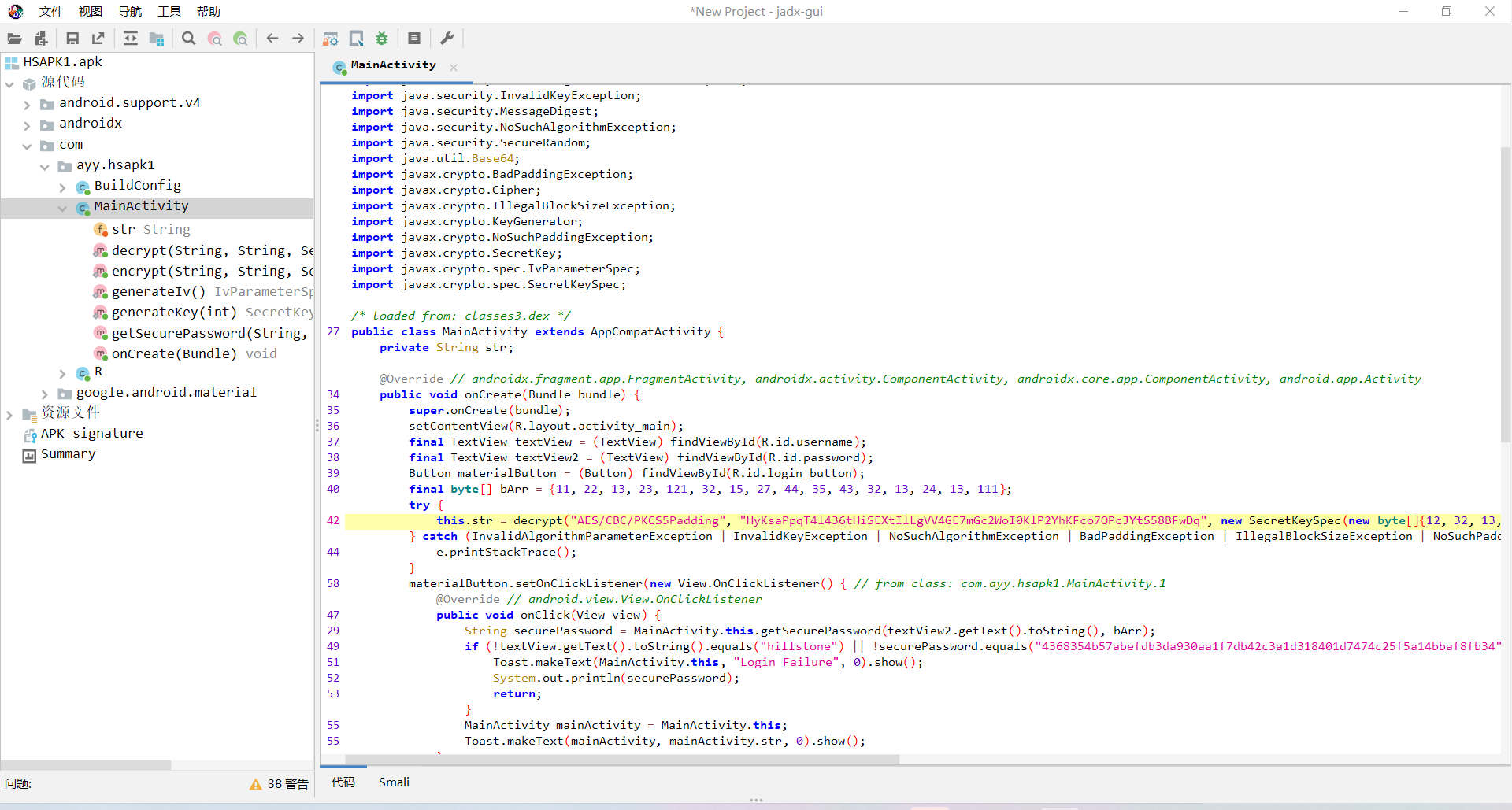
网上找了个脚本,AES解密即可
1 | |
CRYPTO
daobudao
1 | |
strange_chacha
CryptoCTF Aniely原题 参考春哥的wp:https://zhuanlan.zhihu.com/p/545950898
chacha流密码,产生一段密钥流用于加密,类似伪随机数发生器,产生密钥流 。爆破一个短随机数即可。
1 | |
brute_vigenere
密码表里多了一对括号
1 | |
MISC
签到题
公众号回复签到题即可hsnctf{welcome_to_hsnctf}
extract
根据Cloakify.txt名字知道是Cloakify隐写 :https://github.com/TryCatchHCF/Cloakify
得到一个txt文件 根据PK得知为zip文件 改后缀 发现是压缩包套娃
1 | |
解开套娃之后即可得到flaghsnctf{66eec912-e9ce-4e1d-ac54-ecea075dcb96}
外星电波~
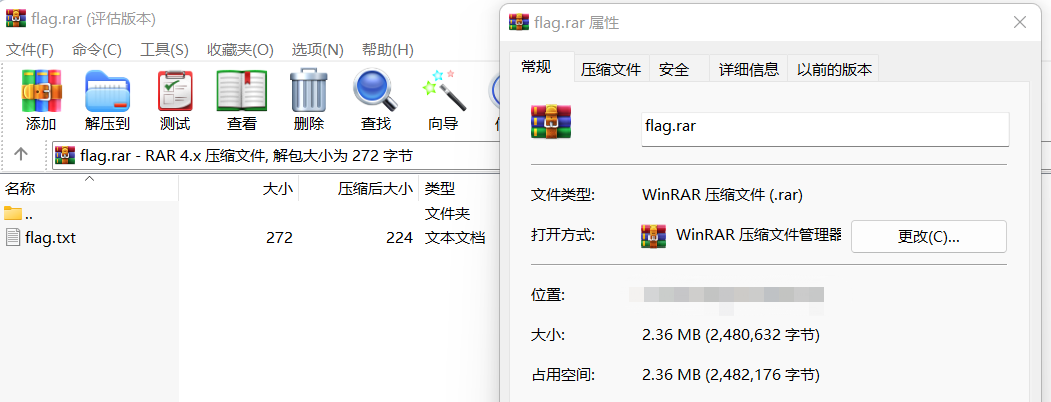
flag.txt比flag.rar小很多怀疑有其他文件 但binwalk无果 在010发现hillstone.wav Ntfs隐写 导出wav文件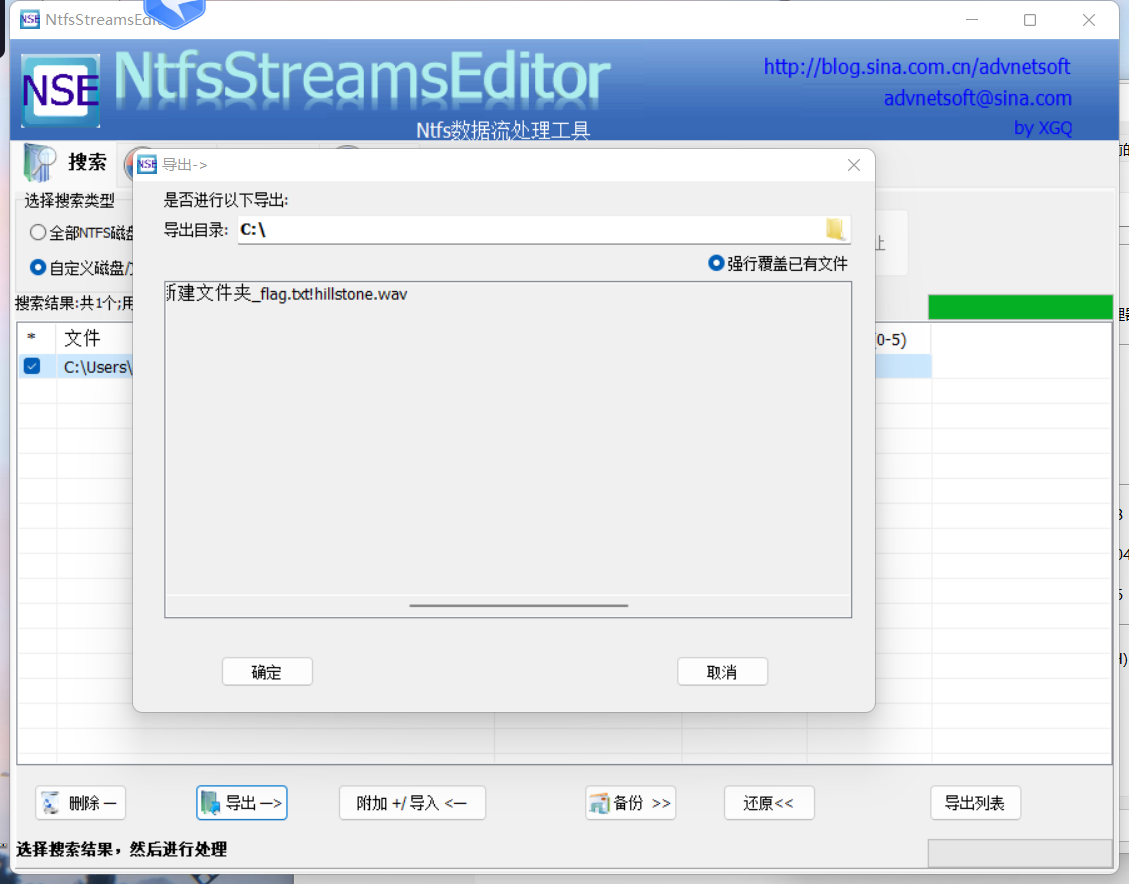
SSTV解密
flag.txt base64转zip文件 解压即可得到flag hsnctf{70995fb0-eb60-0787-f305-77066aeb6730}
WEB
Primitive php
参考:https://blog.csdn.net/cjdgg/article/details/115314651
用Exception和<script>alert("1")</script>绕过payload:?class1=Exception&a=<script>alert('1')</script>&class2=Exception&b=<script>alert('1')</script>&class3=SplFileObject&c=php://filter/convert.base64-encode/resource=hint.php
拿到源码构造payload
1 | |
ICS
S7_analysis
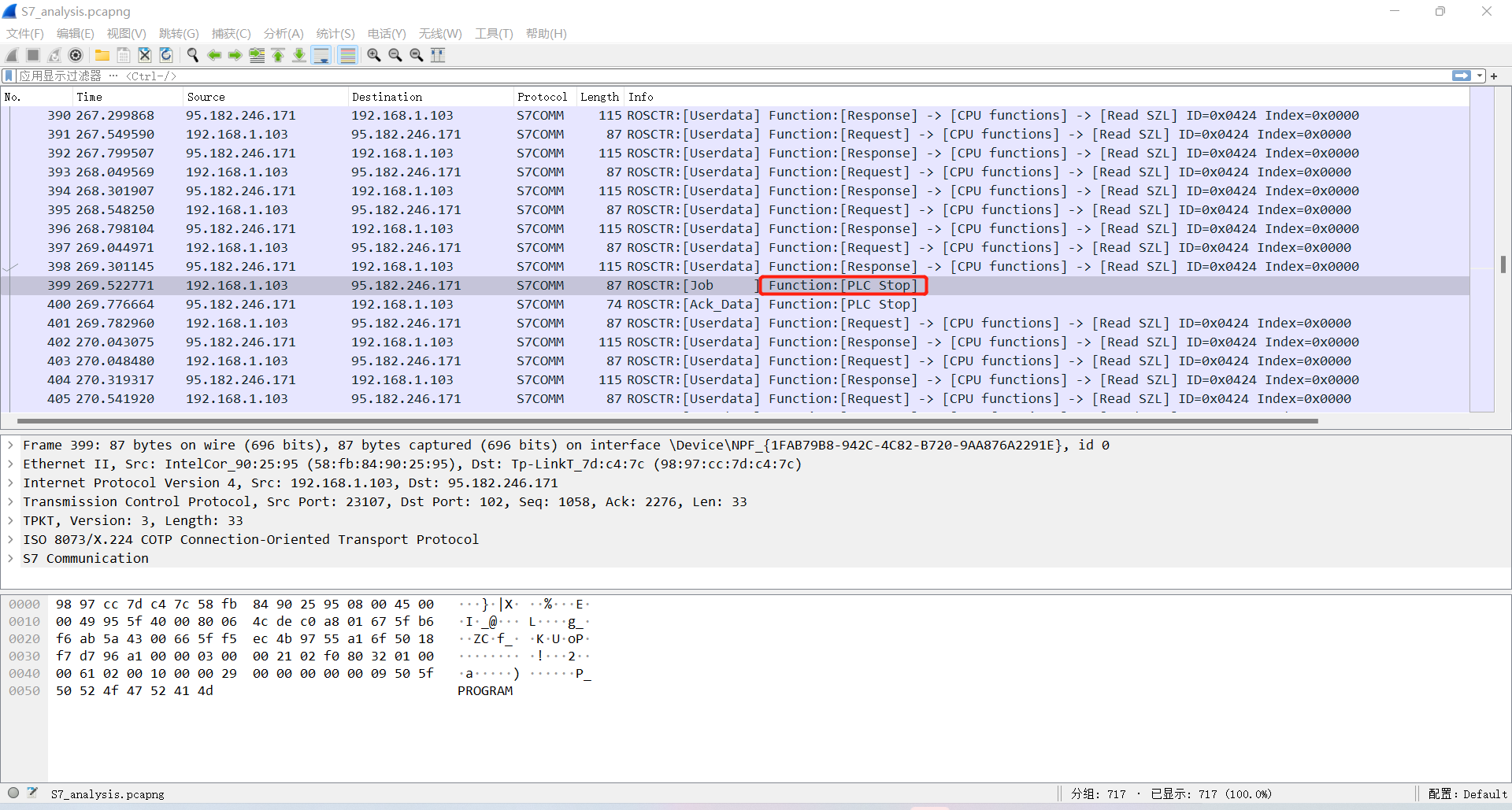
hsnctf{399}