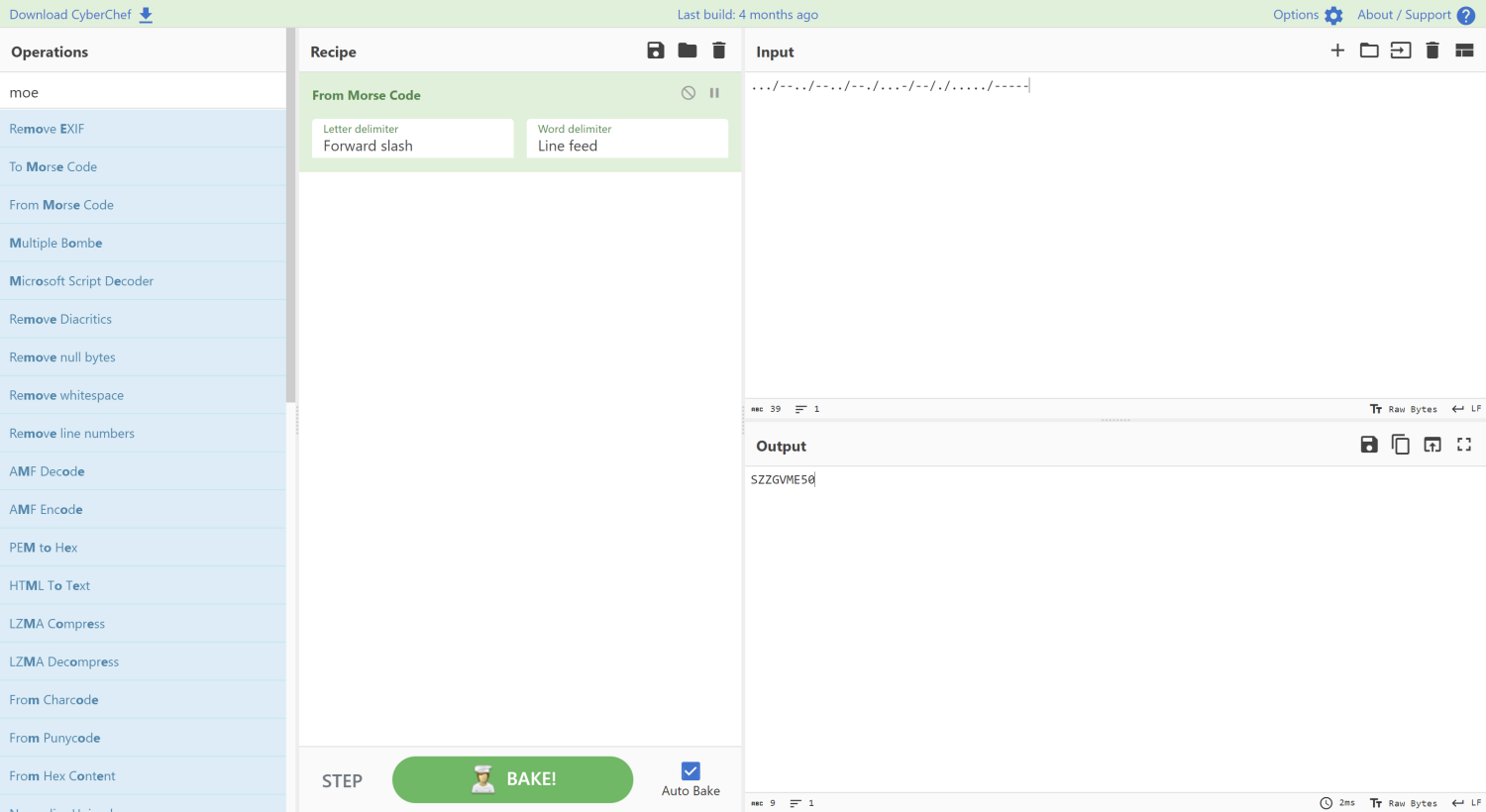
2023数字中国·数据安全产业人才能力挑战赛初赛 Are you ok 题目给了一个日志文件,打开是乱码,但根据其中的明文HUAWEI P10 Plus和Mi Smart Band 5猜测是蓝牙流量,用Wireshark打开。info排序,发现Handle为0x0026的通信最长,符合flag的特征0x00,0x01,0x02三种,猜测是莫斯编码
Value
0x00
0x01
0x02
Morse
.
-
/
写脚本将所有通信过程打印出来,并转化为Morse电码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 import pyshark'1.pcap' , display_filter = 'btatt.opcode == 0x52' )'' for pkt in pcap:str (pkt.btatt.value)if opcode == '00' :'.' elif opcode == '01' :'-' elif opcode == '02' :'/' print (flag)
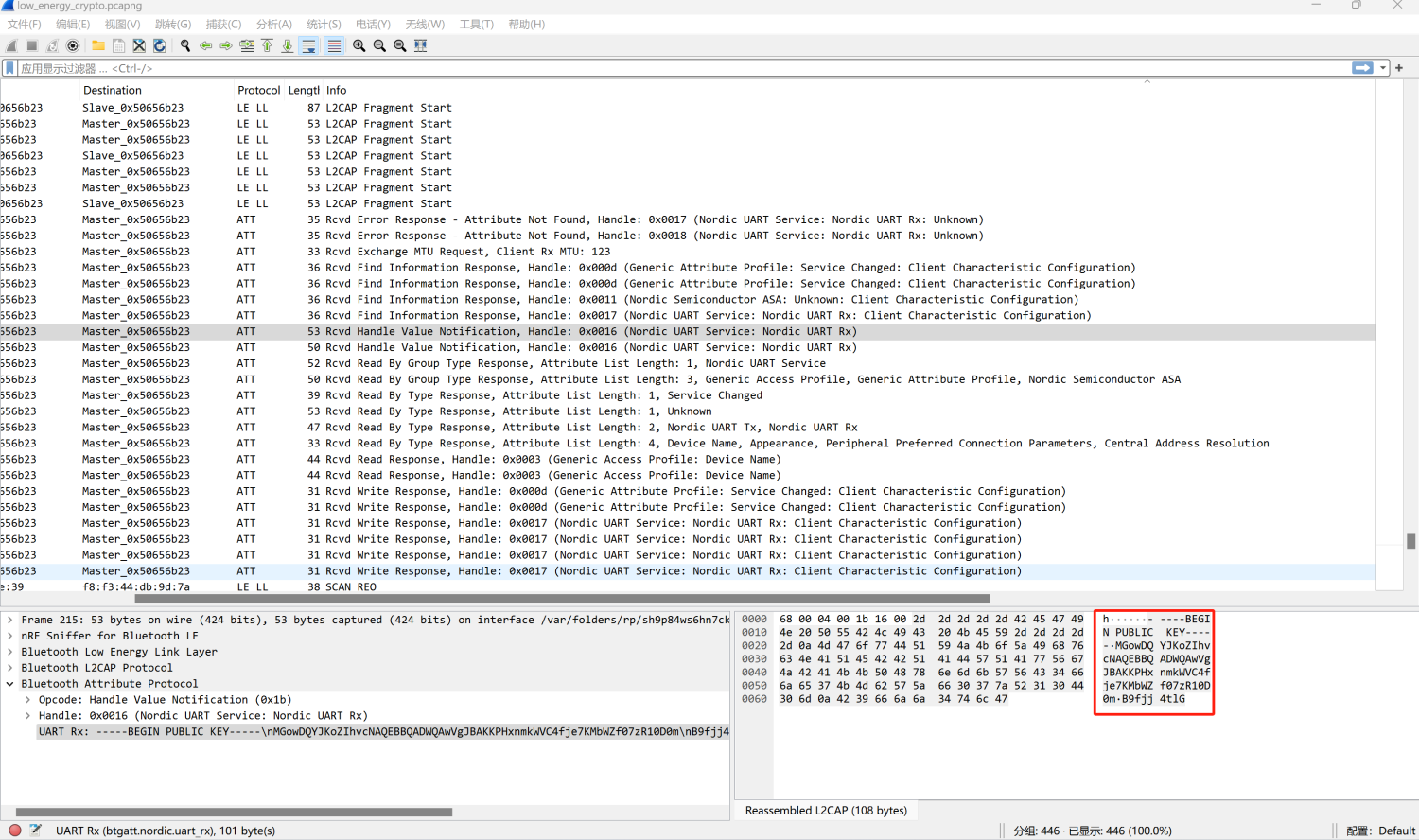
Cyber Apocalypse 2021 Low Energy Crypto 直接根据info排序,发现Handle为0x0016的通信中有一个RSA的公钥
1 2 3 4 5 -----BEGIN PUBLIC KEY -----3L i4l +RI2g0FqJvf3ffEND PUBLIC KEY -----
用openssl转换一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ┌──(g0at㉿kali)-[~/桌面]in 2.key -text -inform PEM -pubinfc :24:6c:e0:60:94:56:6e:87:a4:df
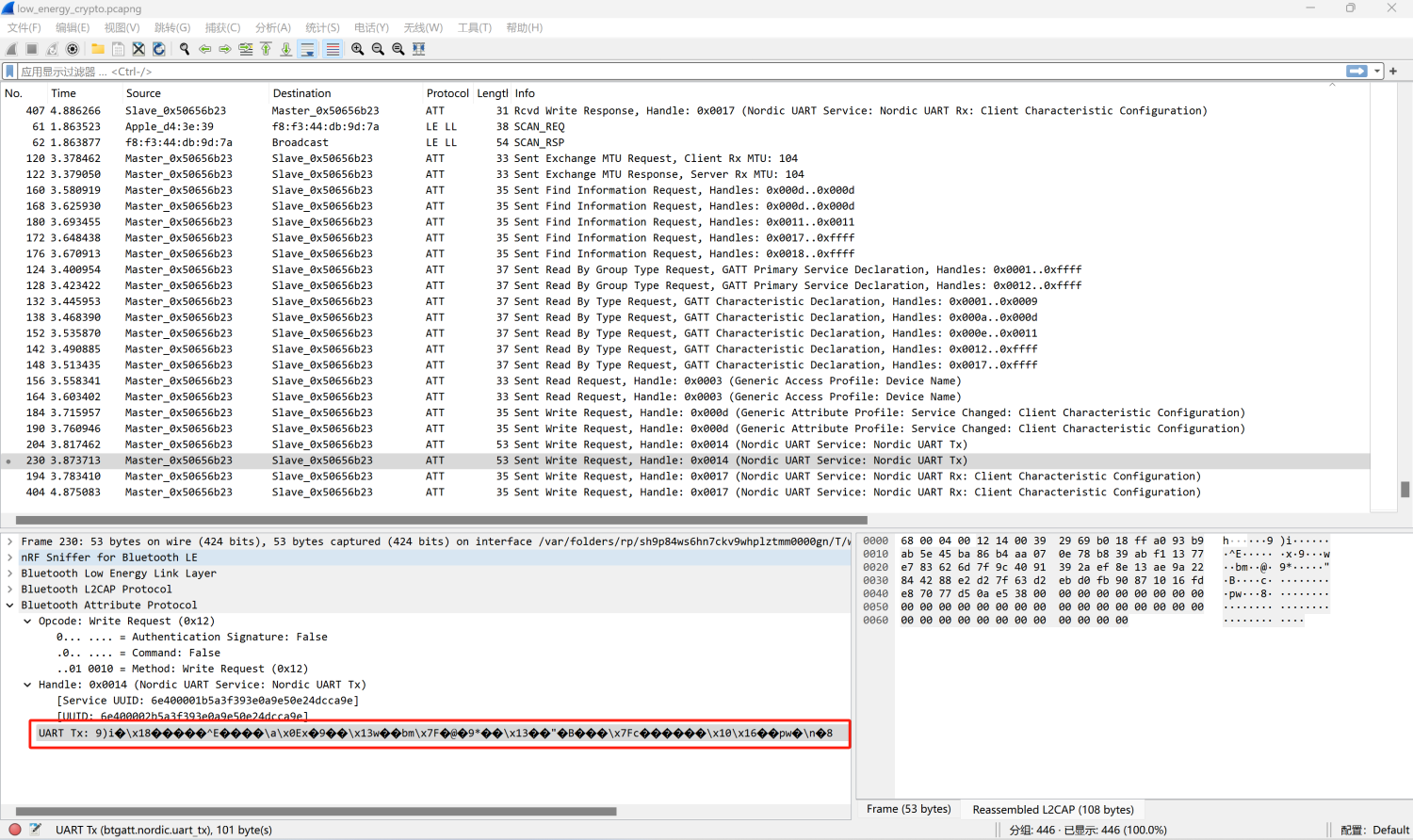
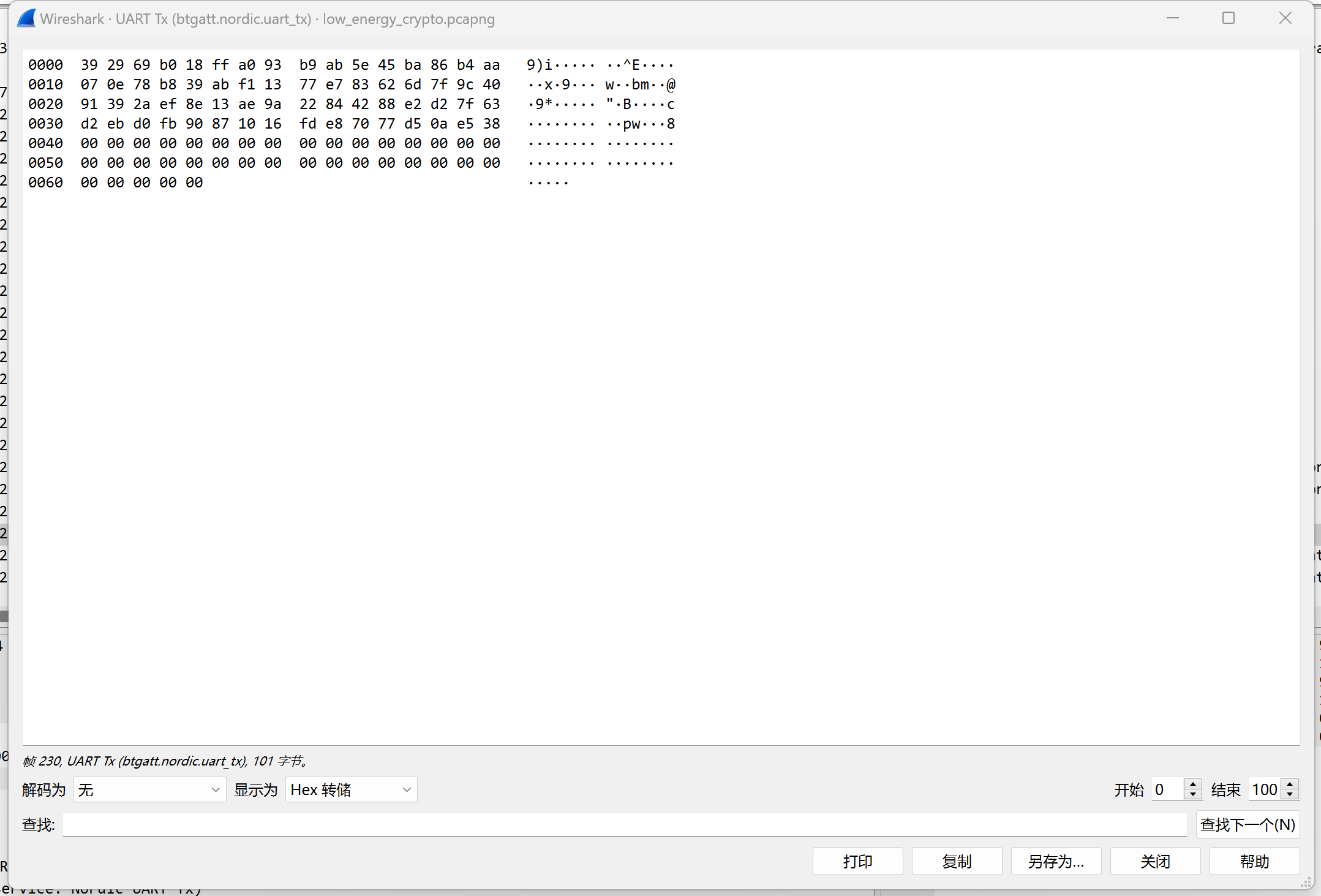
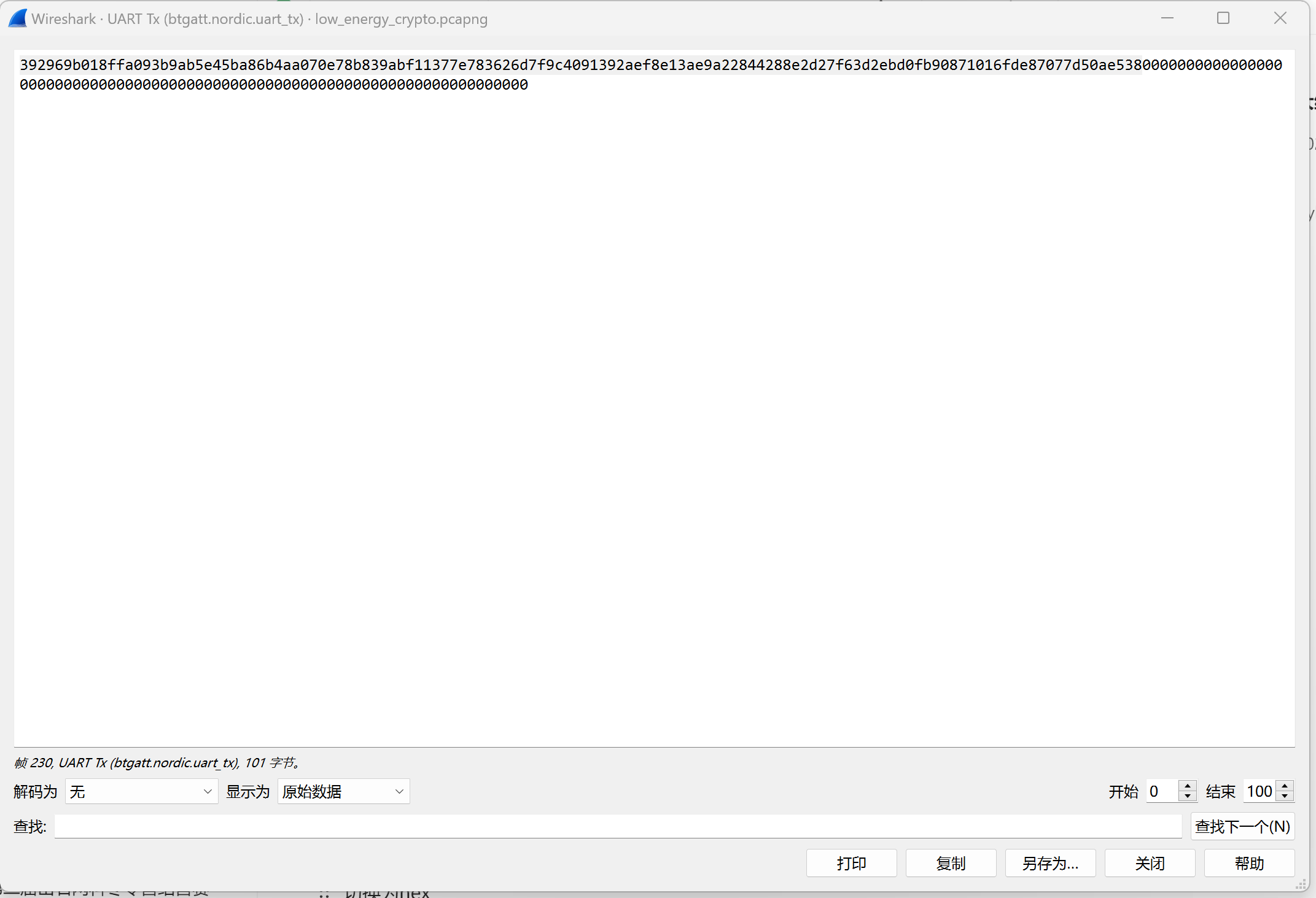
往下看,在Handle为0x0014的通信中发现密文
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 s = """ 00:a2:8f:1f:19:e6:91:65:42:e1:f8:de:ec:a3:1b: 59:97:f4:ef:34:75:d0:3d:26:07:d7:e3:8f:8b:65: 1a:43:ce:5b:e7:fc:24:6c:e0:60:94:56:6e:87:a4: 72:76:5f:89:0a:cb:46:10:37:44:49:f5:95:42:a4: 44:09:d4:a8:09 """ """ 00:cb:ff:72:e2:e2:5f:91:23:68:34:16:a2:6f:7f: 77:df """ "392969b018ffa093b9ab5e45ba86b4aa070e78b839abf11377e783626d7f9c4091392aef8e13ae9a22844288e2d27f63d2ebd0fb90871016fde87077d50ae538" ':' , '' ).replace('\n' , '' )':' , '' ).replace('\n' , '' )int (n, 16 )int (e, 16 )int (x, 16 )92270847179792937622745249326651258492889546364106258880217519938223418249279 92270847179792937622745249326651258492889546364106258880217519938223418258871 import libnumfrom Crypto.Util.number import *1 )*(q-1 )pow (c,d,n)print (long_to_bytes(m))
CVVD 2022智能网联汽车漏洞挖掘赛 蓝牙钥匙的春天 一个蓝牙流量包,随便翻翻发现存在 SMP 协议,全称是 Secure Manager Protocol,是蓝牙用来定义配对和密钥分发的,具体可以看这篇文章http://t.csdnimg.cn/VMihl
另外可以注意到这里使用了BlUETOOTH_LE_LL帧。
由于配对后的流量是被加密的,所以这里看不到他们传输了什么信息,但是有个工具 crackle 是可以解密这种数据包的,这个工具解密蓝牙流量有三个前提,这也在官方的 FAQ 中提到了:https://github.com/mikeryan/crackle/blob/master/FAQ.md
When should I use Crackle?
Crackle is useful when you have sniffed a BLE connection that uses Link Layer encryption and LE Legacy pairing. Before attempting to use Crackle, it’s worth asking the following questions:
Can I log the data without having to sniff it at all?
If not, is my device actually using Link Layer encryption?
Is the device using Legacy Pairing or LE Secure Connections?
If the answers to these questions are “no”, “yes”, and “legacy pairing”, Crackle is the right tool for the job.
翻译一下就是:使用链路层加密和 LE Legacy 配对的 BLE 连接时,Crackle 非常有用。
1 2 3 4 5 6 7 8 9 git clone https://github.com/arunima06/crackle.gitcd crackle
使用添加了BlUETOOTH_LE_LL帧支持的老哥的工具解密流量
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 g0at@Ubuntu22:~/桌面$ crackle -i uploads_2022_04_11_h5kAcZEg_ble.pcapng -o de.pcapng
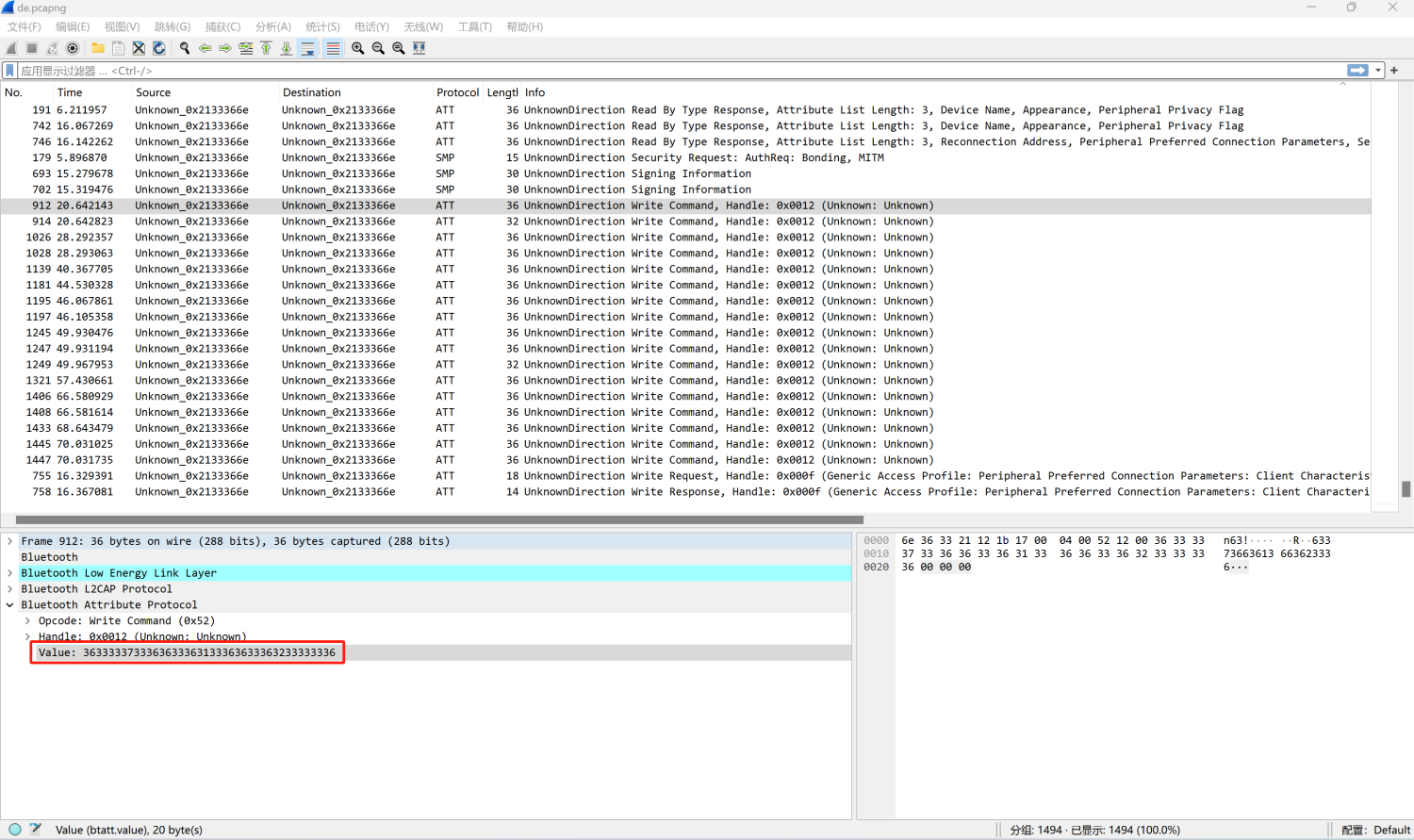
再打开解密后的流量包,可以看到Handle为0x0012处已经有数据
拿到赛博厨子的魔术棒显示,解两次Hex就是字符串,另外发现Value有一些重复
然后就是基于GPT的exp构造
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 import pyshark'de.pcapng' , display_filter='btatt.opcode == 0x52' , tshark_path='D:/Wireshark/tshark' )for pkt in pcap:if hasattr(pkt, 'btatt' ) and hasattr(pkt.btatt, 'value' ):':' , '' )'\n' set (values))print ('' .join (values))for value in values:'utf-8' )'utf-8' )print (final_decoded_value)'' ' 3337333333363335333236333330363536353330 3636364336313637374233393632363133333339 33343334333136323634333433303744 3633333733363633363133363633363233333336 73652c0ee0 c76ca6cb36 flag{9ba39 441bd40} ' ''
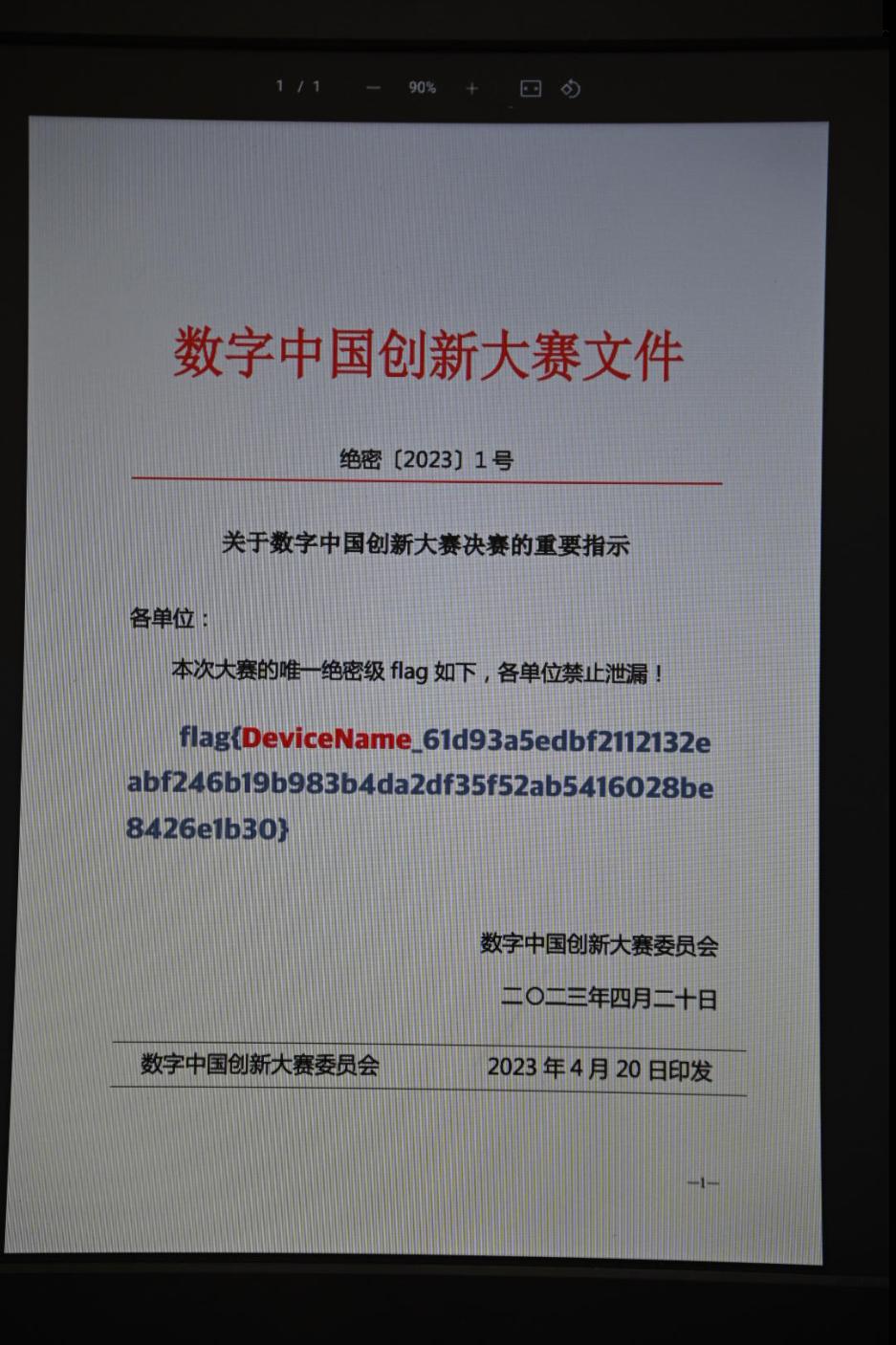
2023数字中国·数据安全产业人才能力挑战赛决赛 AreYouOK Pro 仍然是给了一个日志文件,用wireshark打开,简单过一遍应该是尼康相机向HUAWEI P30 Pro发送了一个文件,这里用了RFCOMM协议【蓝牙RFCOMM 协议】-CSDN博客
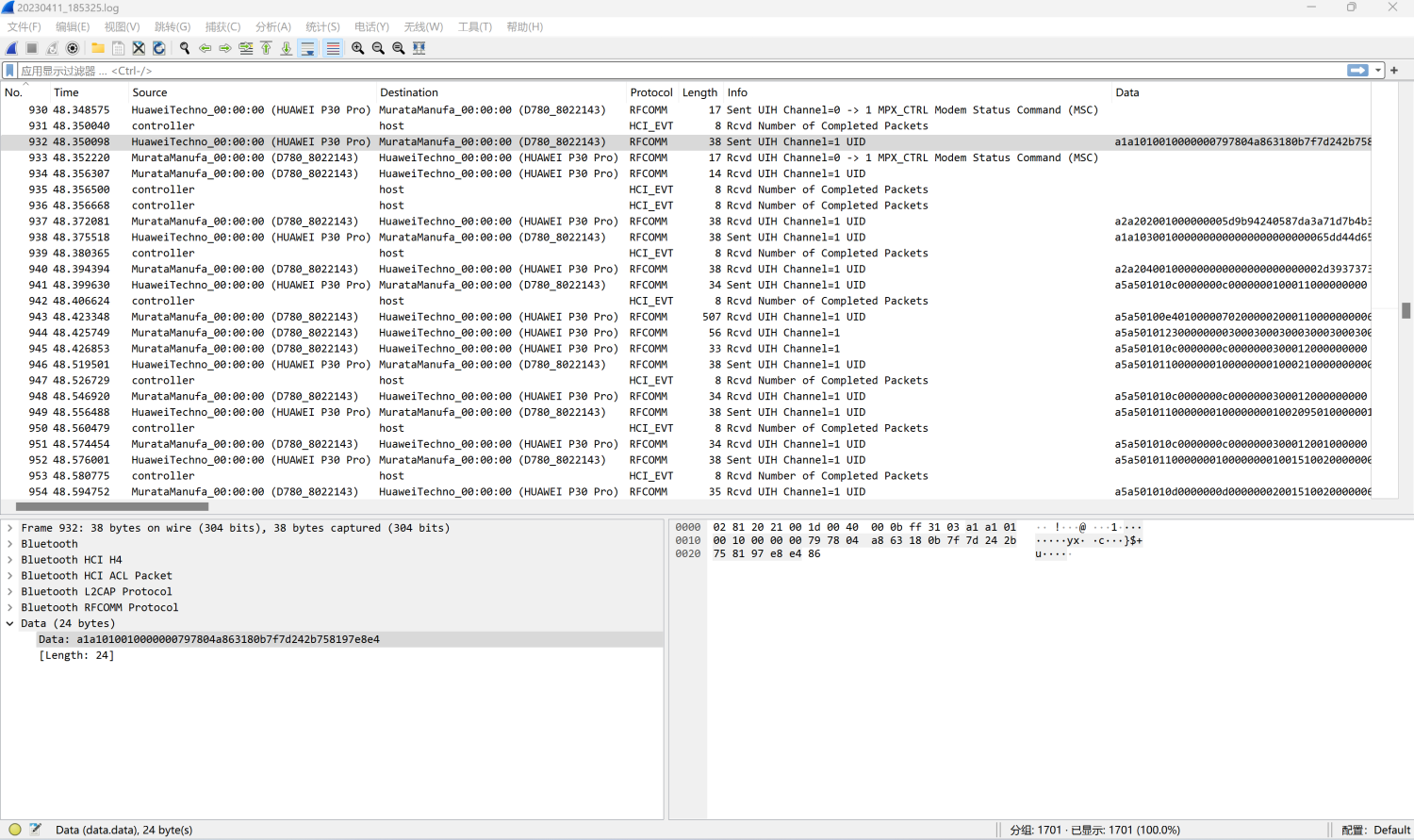
往下看,从932帧开始有数据在传输,
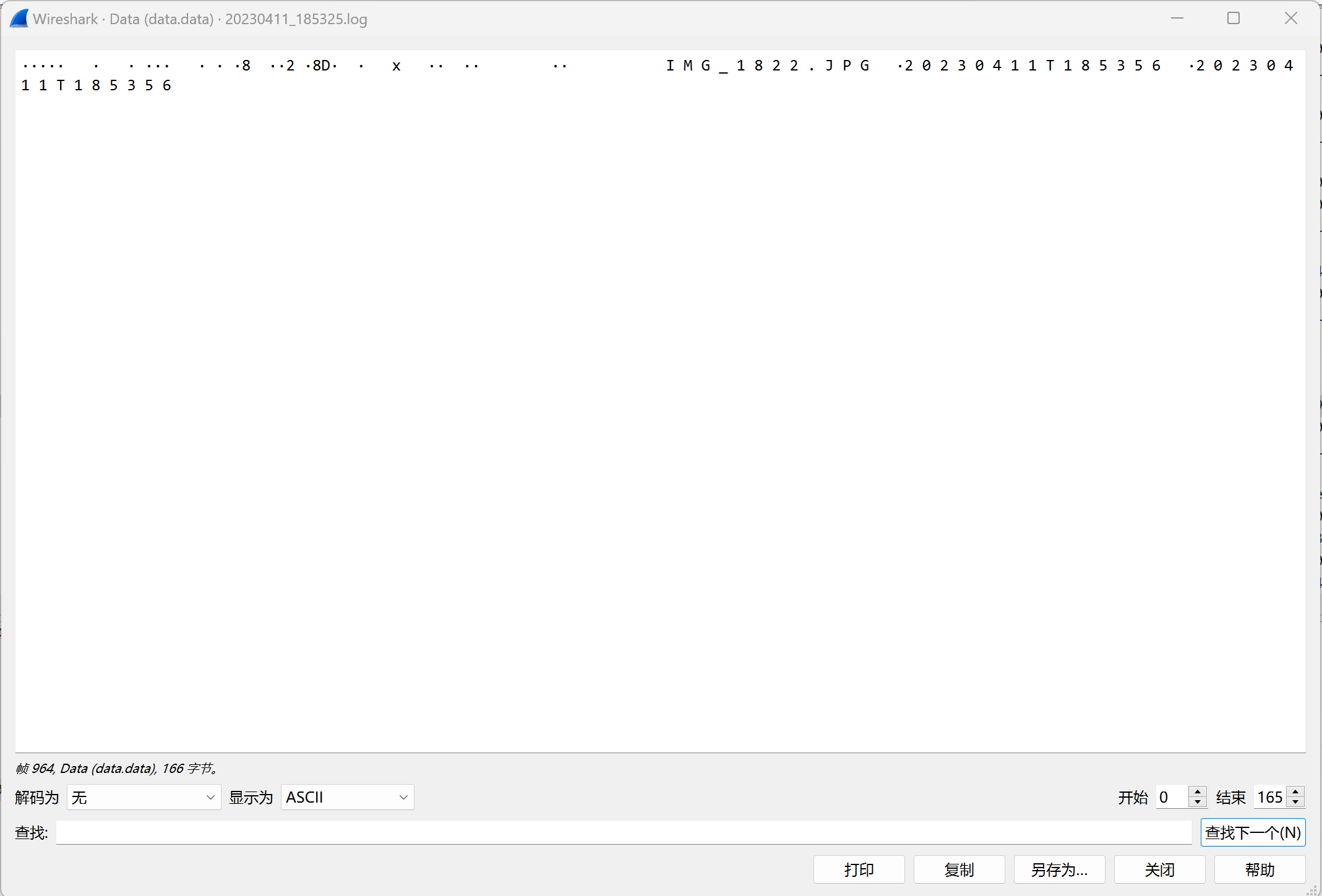
在964帧,确定为传输的是一张jpg图片
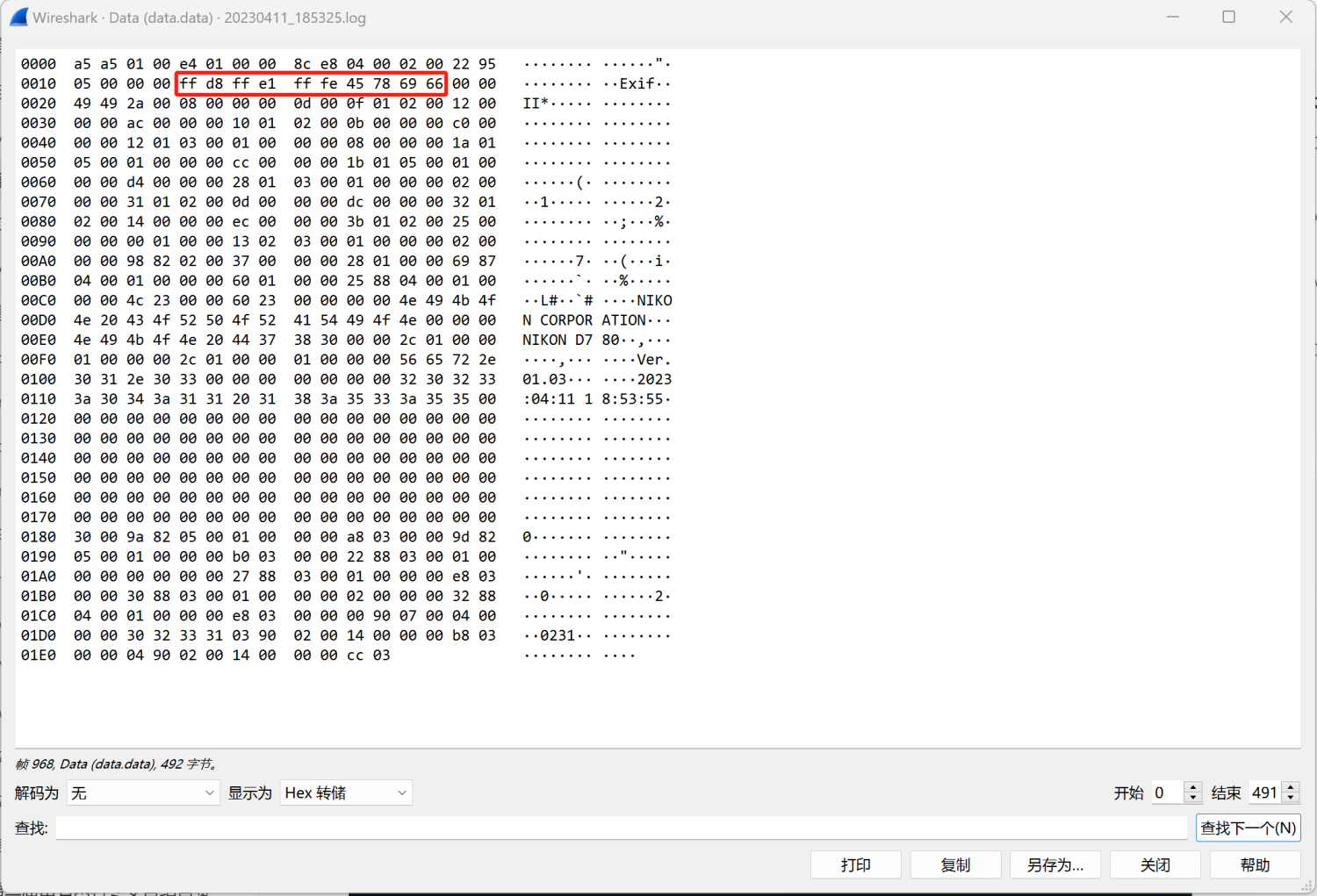
看到了jpg的文件头,所以图片从968帧开始传输
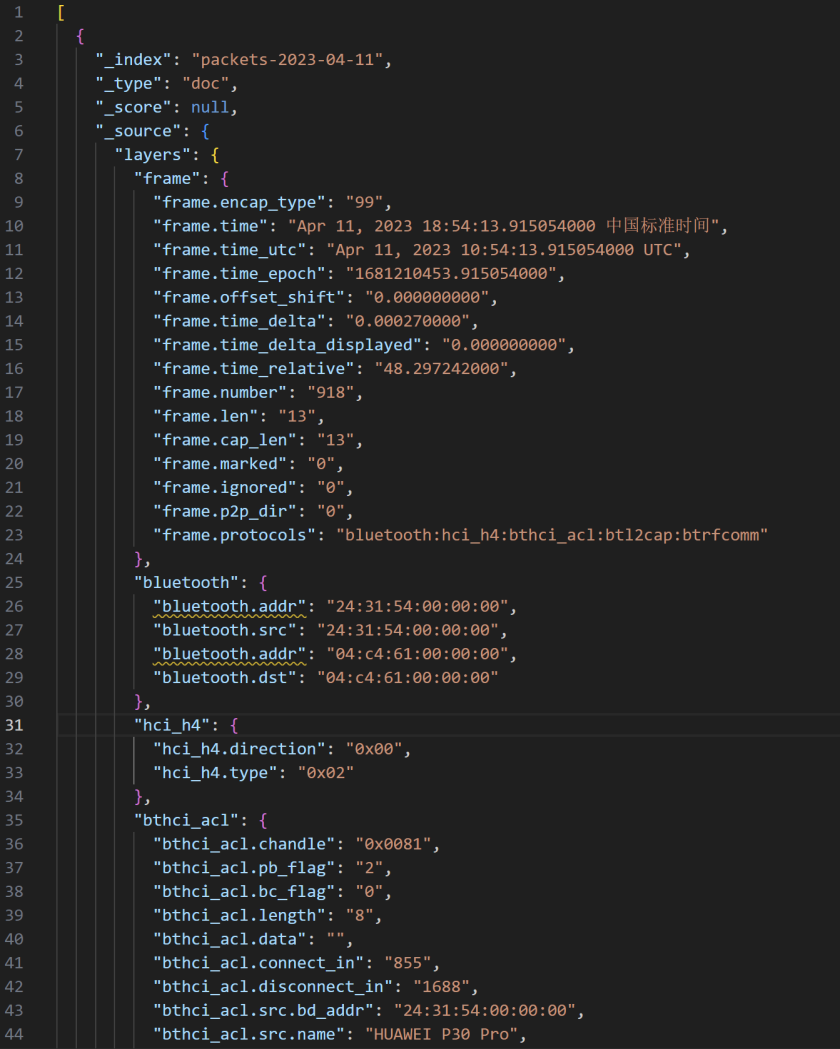
观察Data数据发现,后面的长度均为680(猜测这是单个数据块最大值)在jpg文件头前还有一段数据,猜测传输过程是将文件分块传输,每块前均有固定的传输标识符,翻看Data数据,在下面也多次发现a5a50100这段数据,_ws.col.protocol == "RFCOMM"筛选出RFCOMM传输数据的过程,导出分组为json文件。
根据json文件格式写脚本,从”frame.number”: “968”图片正式传输开始读取数据
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 import json"1.json" , "r" , encoding='utf-8' ) as f:"" for packet in packets:"_source" ]["layers" ]if "frame.number" in layers["frame" ] and int(layers["frame" ]["frame.number" ]) >= 968:if "data" in layers:"data" ]["data.data" ].replace(":" , "" )"a5a50100" )"" for x in data:"flag.jpg" , "wb" ) as f:
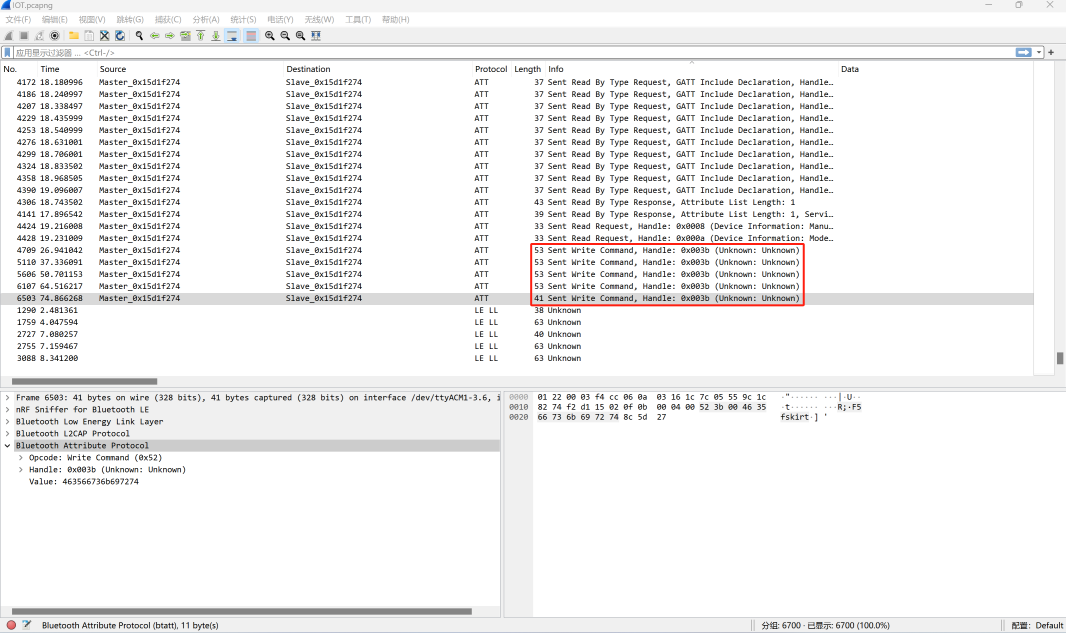
第七届工业信息安全技能大赛车联网安全锦标赛 GAGA TT 这个就太简单了,一眼丁真,数据在Handle为0x003b中,套用上面的脚本直接梭哈
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 import pyshark'IOT.pcapng' , display_filter='btatt.opcode == 0x52' , tshark_path='D:/Wireshark/tshark' )for pkt in pcap:if hasattr (pkt, 'btatt' ) and hasattr (pkt.btatt, 'value' ):':' , '' )'' .join(values)bytes .fromhex(values_str).decode('utf-8' )print (values_str)