第四届“长城杯”网络安全大赛
Web
SQLUP
爆破得到账号admin 密码1
发现文件上传过滤了字母p
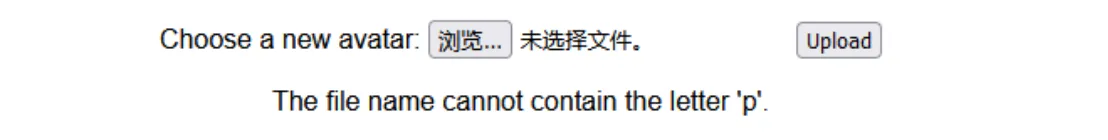
上传.htaccess:AddType application/x-httpd-php .txt 解析.txt为php
传一句话木马
tac /flag得到flag
Pwn
FlowerShop
1 | |
Kylin_Heap
1 | |
Reverse
easyre
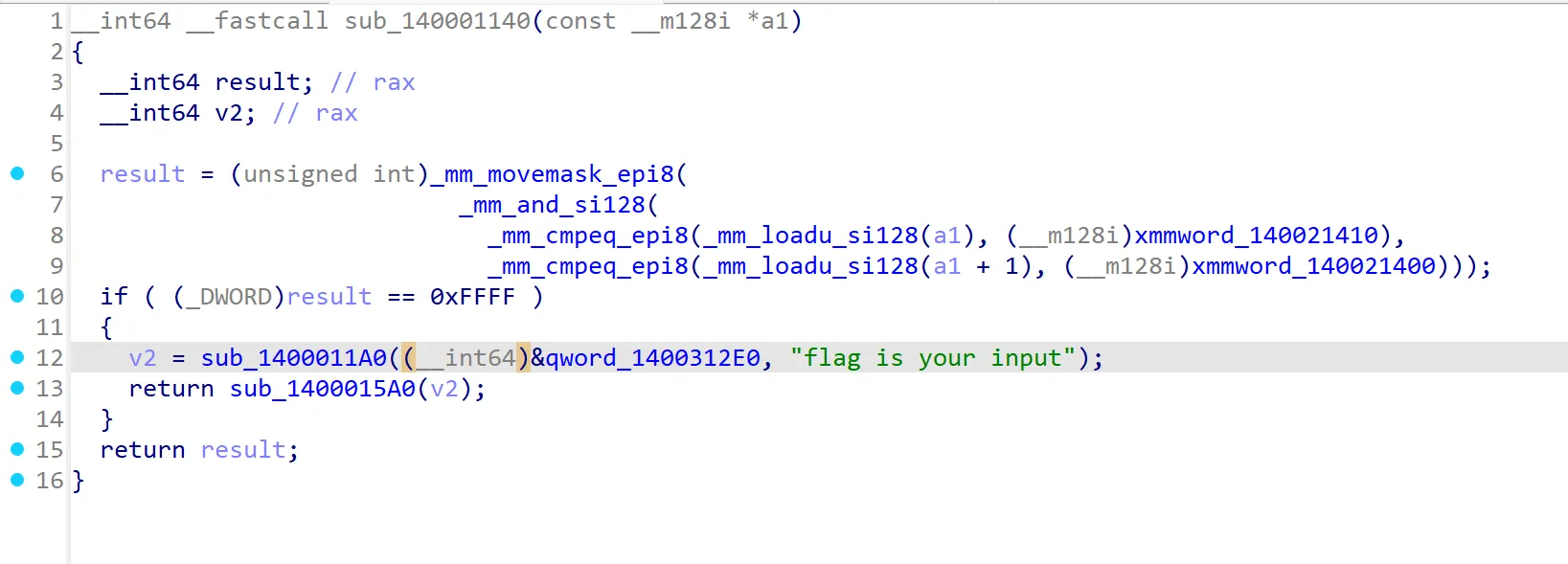
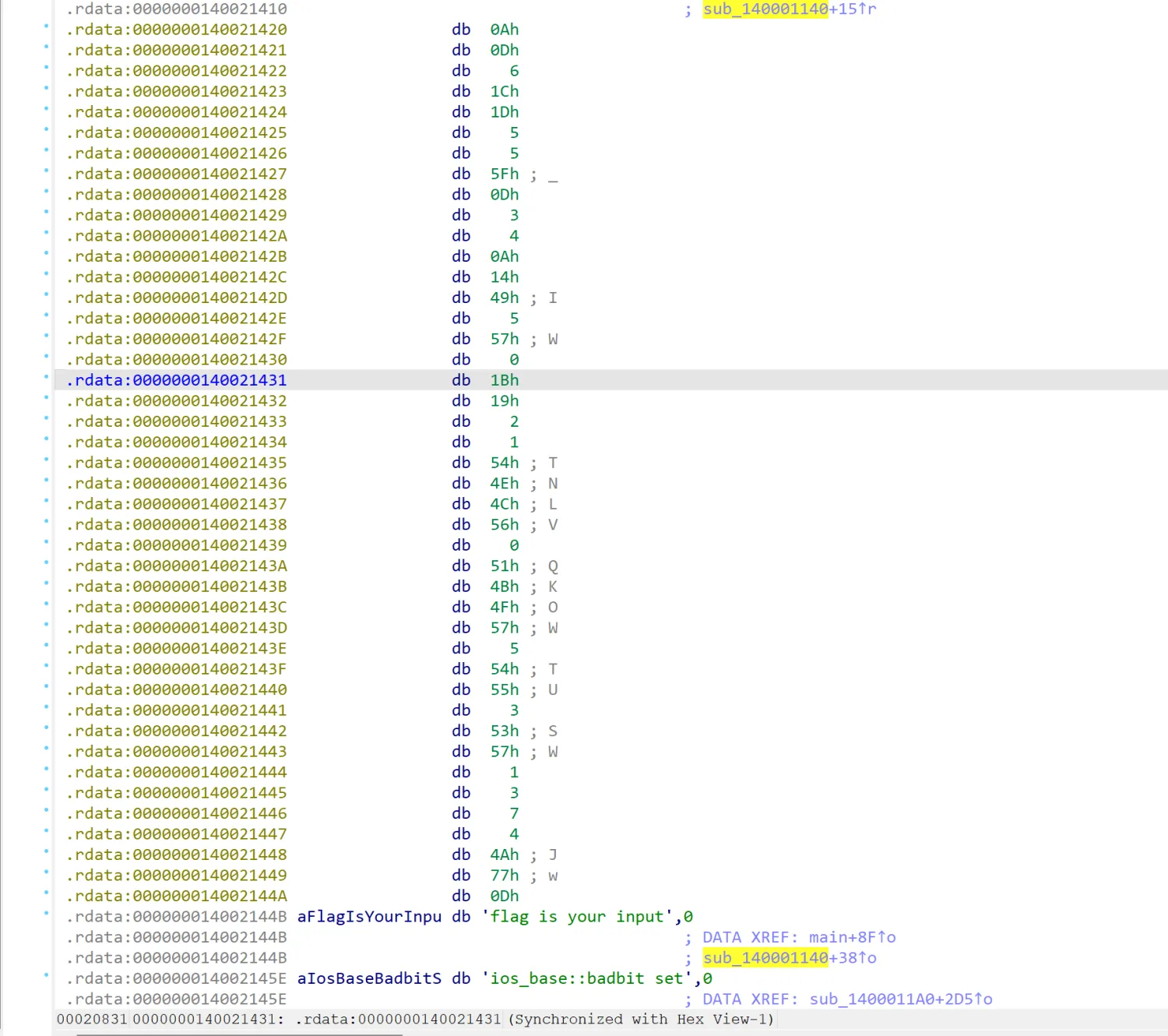
1 | |
Crypto
RandomRSA
通过LCG的递推公式,可以得到:
$$
X_{n+1} = aX_n + b \pmod p \
n = pq = (X_n + \epsilon_1)(aX_{n} + b + \epsilon_2) \
$$
显然这是在
$$
Z^*_p
$$
下关于
$$
X
$$
的 二次方程。如果没有 next_prime 这个函数增加的小量
$$
\epsilon
$$
,那么直接解这个方程就能得到
$$
X
$$
。
但是由于有这两个误差,而经过测试,发现这个误差是完全可预测的,大概在
$$
(0,1000)
$$
这个范围,所以可以利用这个来爆破计算
$$
X
$$
。
1 | |
即
$$
aX^2 + (b + e_2 + ae_1)X + (be_1 + e_1e_2 - n) = 0 \pmod p
$$
这里可以使用 sagemath 的 roots 进行爆破,但是由于 roots 但是解根的时间是比较久的,所以可以采用求根公式,验证
$$
\Delta = B^2 - 4AC
$$
是否在
$$
Z^*_p
$$
下正好是二次剩余,以减少爆破的次数。
1 | |
Misc
BrickGame
漏洞探踪,流量解密
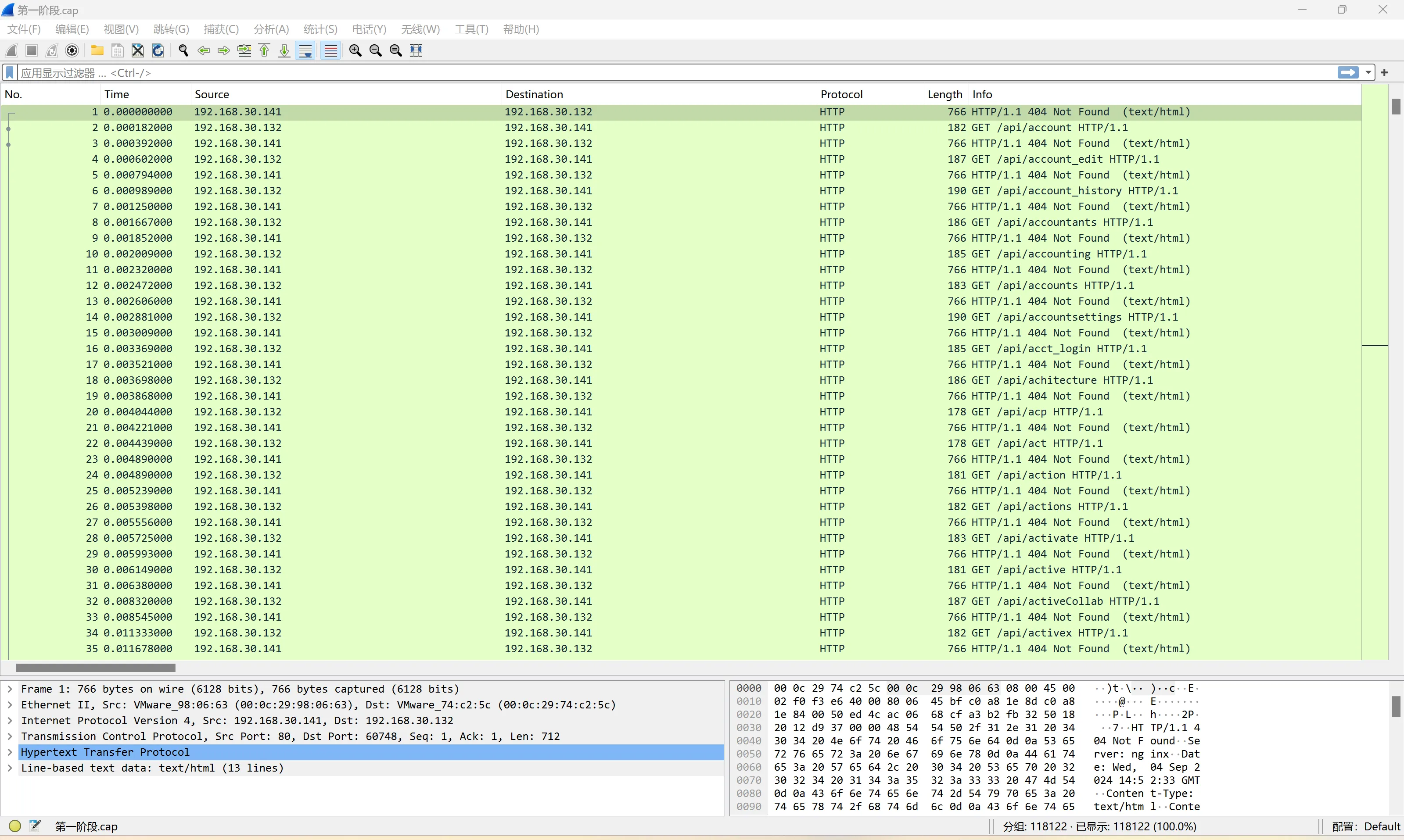
根据题目信息和流量包掩码爆破192.168.30.xxx;得到压缩包2的解压密码是192.168.30.234
筛选http流得到RC4hint
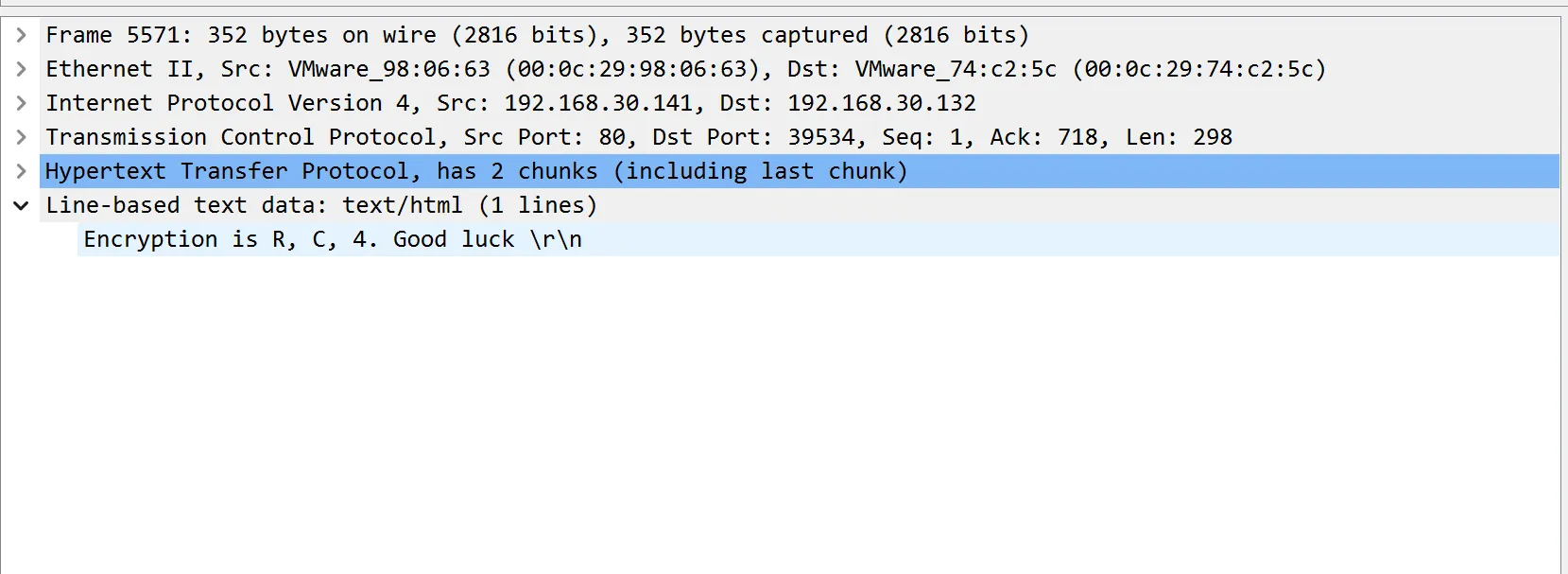
逐行查阅http流,找到rec的密文和key
1 | |
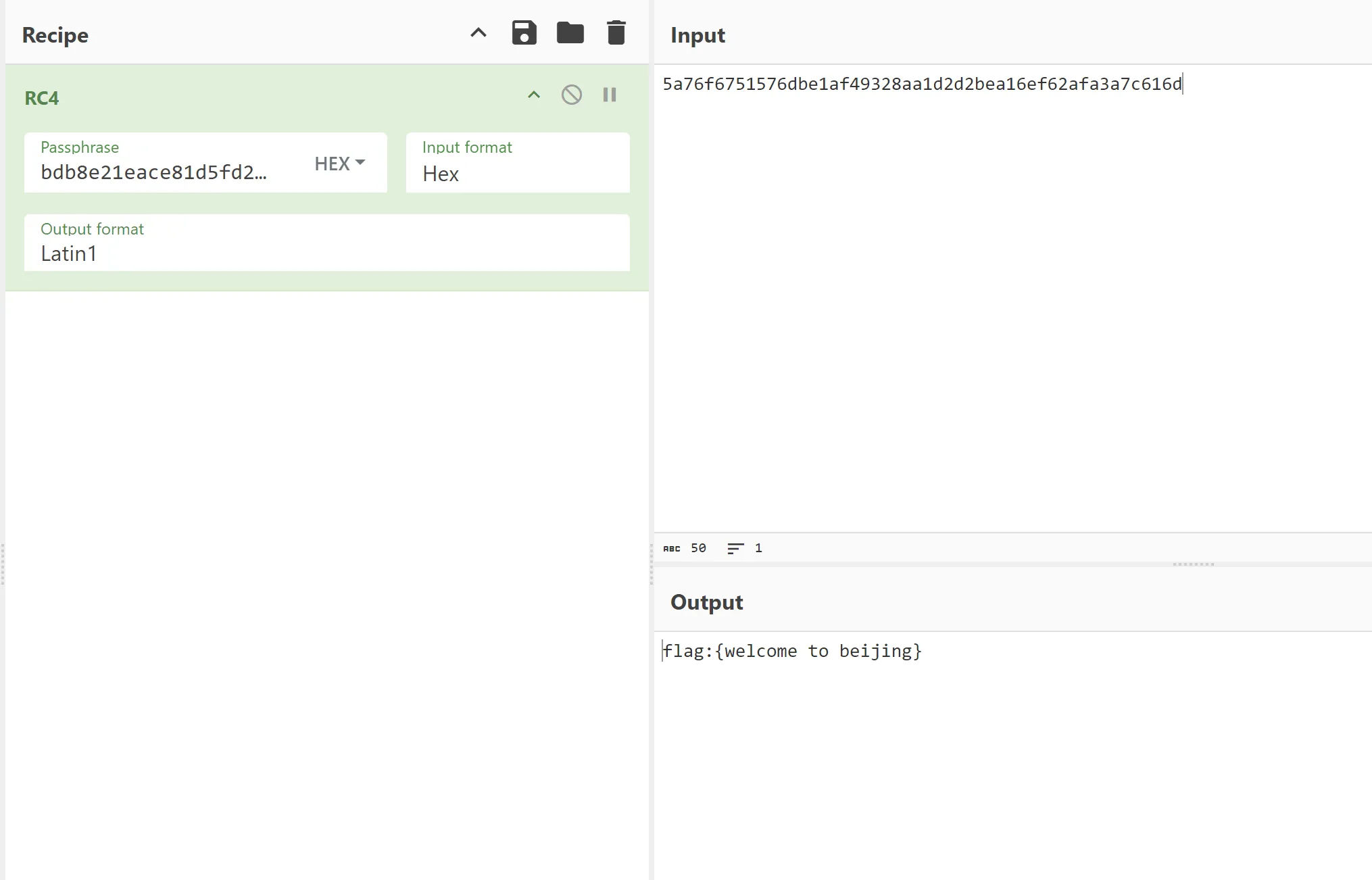
最安全的加密方式
导出保存为rar文件
1 | |
解压得到一堆md5 挨个解密即可
1 | |
第四届“长城杯”网络安全大赛
https://g1at.github.io/2024/09/08/ccb2024/